NOTE: The Information contained in this Article is only Intended for Educational Purposes for checking the security of your network. I take no Responsibility for the misuse of this information and the harm brought to you or any one else (specially your neighbour.. :)
The Stuff that you are going to need is
(1) Backtrack (You can get it here)
(2) Wireless Card that Supports Packet Injection
Before we Start, I take it for Granted that you are aware of a Few things...
I Hope You already have a Live CD, Bootable USB or a Virtual Backtrack Installed in your System. In case of Virtual Machine, You will need an External Wireless Card. And in case you don't already have Backtrack, I suggest you bookmark this page and get it first.
Also, I hope you have googled by now to see if your Wireless Card will support Packet Injection or not. Again, if you haven't already done that go and get this done first :)
Now that we are Ready.. Lets Begin..
If You are Using a Boot CD, As in my case, You will see the folllowing screen when the CD Loads.
Just Select "Start BackTrack FrameBuffer (1024x768)"
or Select "Start BackTrack FrameBuffer (800x600)"
Depending On your Display Settings. These Options are to get to the GUI of Backtrack.
What will follow next is the Loading of all Drivers and Other Processes. Once they come to a halt. You will See a Cursor. Just Type in "startx".
Once, the Startup is Completed you will be at the Desktop of Backtrack
Now, We better get our Network Interfaces Started. While there are a few ways of Doing that. The simplest way is through the Menu.
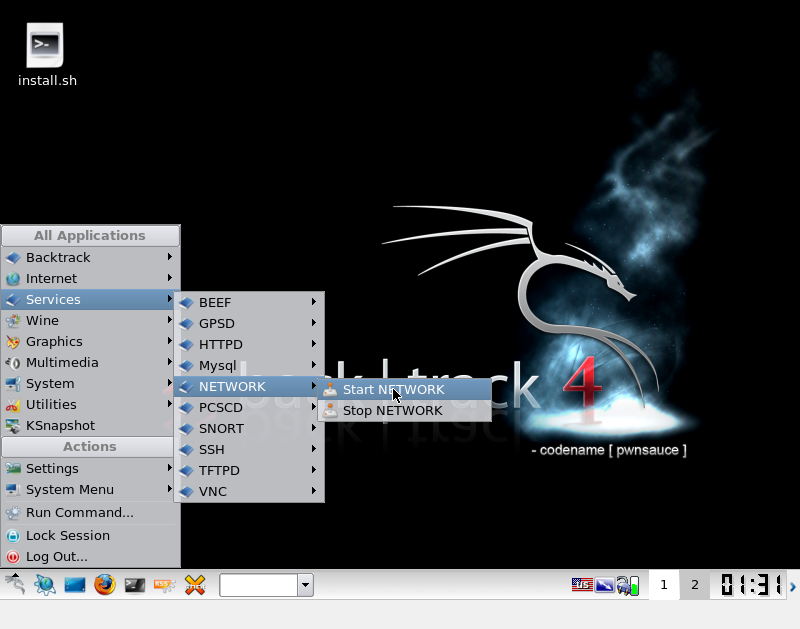
Once, Network has been Started. We need to go Start a Konsole. Which we will be using to enter all commands to crack wep.
Once, inside the Konsole. Type in "iwconfig" to see the status of all the network interfaces of your Machine.
In My Case, My Wireless Interface is "wlan0". In your case, It can be any other or might just be wlan0. Remember, whatever your interface, replace my "wlan0" with it throughout the Tutorial now.
Now that we know the Interface, we better put it on monitoring mode. To do that, we need to type this command.
airmon-ng start wlan0
Press ENTER and You will see that monitor mode for your Wireless Interface will be enabled now. In my case, the monitor mode has been enabled at "mon0". This will be our new Interface now not "wlan0".
Now that the monitor mode has been enabled. We will scan our Area for any WEP Encrypted Wifi Networks. To do that we need to type the following command.
airodump-ng --encrypt wep mon0
What you will see Next will be A List of All the WEP Encrypted WIFI Networks around you. There are some details in there too. Here's a simple explanation of a few of them
BSSID = MAC Address of the slave (Most Important)
PWR = Signal Strength
CH = Channel Number
ENC = Encryption Type
ESSID= Name of slave's Network
#Data = Amount of IVS Collected (Most Important)
#/s = IVS Per Second
You Might just wanna copy the BSSID as it is going to be used a lot.
Our slave's Details
BSSID= 00:50:F1:12:12:10
CH = 1
ESSID= {censored}
Something, You might wanna know but is not useful for WEP is that the "STATION" are the Computers currently connected to the Network. As you can notice, My slave currently has a Computer connected to it.While STATION is important for WPA Hacking, It is not useful for WEP Hacking.
Now that we have our slave in Sight. It is now time to target our Interface on collecting packets from it. So, now we will make our airodump-ng more specific to target it on our slave's Network.
airodump-ng --bssid 00:50:F1:12:12:10 --channel 1 --encrypt wep --ivs --write wephack mon0
Once You hit ENTER. You will notice that now our Wireless Interface will only focus on Our slave's Network (In this case: 00:50:F1:12:12:10)
Now that we have targeted the slave's Network. It is time to Start gathering Packets from it. There are two ways for Doing it.
(1) Fragment Attack
(2) Arpreplay
Its your Lucky day..lol.. I will be going through both.
But before these attacks, we need to fool the Router into thinking that we are authenticated to receive data from it. To do this we will "fakeauth" the slave's Router.
aireplay-ng --fakeauth 0 -a 00:50:F1:12:12:10 mon0
Once, You hit ENTER you will see something Like this when the Attack is Successful.
02:29:07 Sending Authentication Request (Open System) [ACK]
02:29:07 Authentication successful
02:29:07 Sending Association Request [ACK]
02:29:07 Association Successful :-) (AID: 1)
Now that the Association is Successful. We will initiate the Process to collect Arps. First, We will try Arpreplay as it is a very simple attack. Here's the command.
aireplay-ng --arpreplay -b 00:50:F1:12:12:10 mon0
Once, You hit ENTER you will see something Like this. After a Few Seconds or Maybe a few minutes, You may see the number of arps rise. If that happens ARPREPLAY has been successful or else, We will have to move on to Fragment Attack.
OK. Since, Our Arpreplay has failed we will now initiate a Fragment attack. Here's the code
aireplay-ng --fragment -b 00:50:F1:12:12:10 mon0
Once, You hit ENTER. Out Network Interface will start to collect Packets from The slave's Router. When it asks you to use a particular packet. Just hit Y and press ENTER.
It will now try to capture 1500 bytes of Keystream. This keystream will be stored in a XOR file as in my case- fragment -0123-023217.xor We will later use this very captured keystream to forge it into a packet using packetforge-ng.
Basically, what we are going to do is use that keystream and make a valid packet out of it. Then we will use that packet to arpreplay our slave's Router. So, Lets make a packet then..
packetforge-ng --arp -a 00:50:F1:12:12:10 -h 11:22:33:44:55:66 -l 255.255.255.255 -k 255.255.255.255 -y fragment-0123-023217.xor -w wepfrag
OK. To keep this command simple let me just say this. Here, "-a" is the slave's MAC Address and "-h" is our MAC Address which I just entered for namesake. Let the rest of the things be the same. For those extra Information Seekers.. You can pm me or just google it.
Just hit ENTER and there we go, the Packet has been made.
Now, We will use this packet to arp attack the slave's Router. Here's the Command.
aireplay-ng --arpreplay -r wepfrag -b 00:50:F1:12:12:10 mon0
Just hit ENTER and the Mag!c Finally begins...
Now, Its Time to Play Wait & Watch... Just Wait till the #Data Table reaches 30000 or close...
Once, You have enough #Data Packets. It is time to Initiate the Final Kill. aircrack. Here's the command.
aircrack-ng wephack-01.ivs
Hit a Final ENTER and See the Process.. Will take a few Seconds or Minutes.. depending on the Password....
And Voila... Here it is....






















